Product Specification |
| Fixed 1G Ethernet port | 8 |
| Fixed 1G SFP port | 1 |
| Fixed 10G SFP+ port | 1 |
| Management port | 1 data multiplex port |
| Console port | 1 |
| Warranty period | 3 years |
| USB | 2 x USB 2.0 ports |
| Hard disk | No hard disk for factory delivery, expansion cards supported |
| Hard disk expansion card | 1 TB HDD |
| Expansion slot | None |
| Power supply | 1 for factory delivery |
| Listing time | May 2022 |
Software Specifications |
| To-do items | To-do items on the home page |
| Security overview | Security overview on the home page |
| Device information | Device information on the home page |
| Quick onboarding | Quick onboarding solution (network configuration+license activation) in rapid deployment |
Monitoring center |
| Attack statistics display | Attack statistics display on the monitor page |
| System log | Logs related to systems in log monitoring |
| Security log | Logs related to security in log monitoring |
| Operation log | Logs related to user operations on the web UI in log monitoring |
| Syslog server | System logs sent to a third-party server |
| Session monitoring | Session information (new sessions and concurrent sessions) in traffic monitoring |
| User session count statistics and query |
| Traffic monitoring | Traffic information on different interfaces in traffic monitoring |
| Traffic information on different applications on the entire network in traffic monitoring |
| Device health status | Device health status information (overall score of resources, licenses, and configurations) in device monitoring |
| Hardware health | Hardware information (including CPU, memory, and hard disk information) in device monitoring |
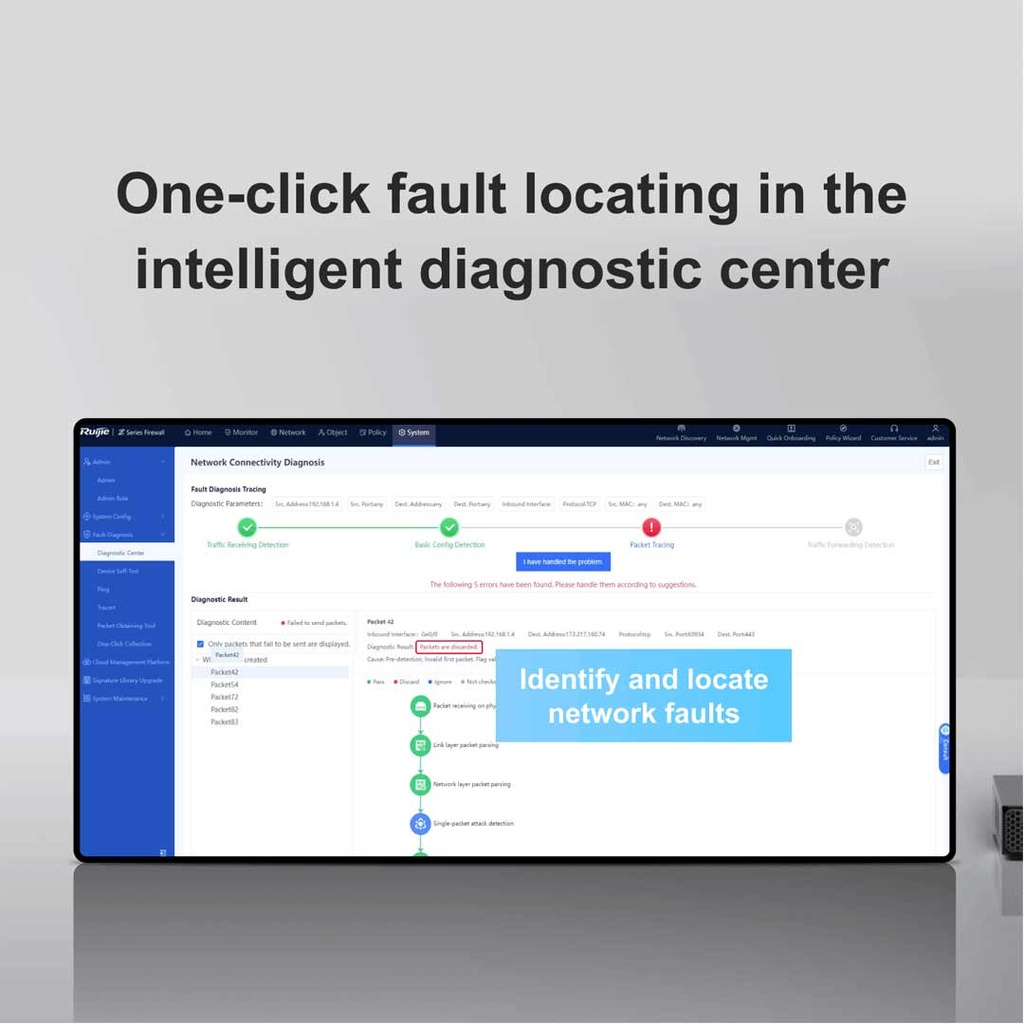
| Service continuity detection navigation | Service continuity detection navigation on the web UI |
| Packet tracing | Packet tracing on the web UI |
| Flow log query | Flow log query on the web UI |
| Packet obtaining for analysis | Packet obtaining for analysis on the web UI |
Network |
| Physical interface | Configuring interfaces as LAN/WAN interfaces; three modes for WAN interfaces: PPPoE, DHCP, and static IP modes |
| Configuring routing or transparent mode for interfaces |
| Sub-interface | Configuring sub-interfaces and VLAN IDs |
| Bridge interface | Configuring interfaces in transparent mode as bridge interfaces |
| Aggregate interface | Configuring aggregate interfaces |
| Static route | Configuring IPv4 and IPv6 static routes |
| PBR | Configuring policy-based routing (PBR) |
| Routing table | Overall routing information of a device; configuring ISP address library routes |
| DHCP server | DHCP server; configuring DHCP address pools |
| Address management list | Assigned DHCP address list |
| DNS server | Configuring DNS addresses for devices |
Object |
| Address/Address group | Configuring address objects in IP address/range format |
| Zone | Configuring security zones |
| Application/Application group | Configuring application types in application/application group format |
| Service/Service group | Configuring service objects; common default port services supported |
| Time plan | Configuring time objects; one-off time plans and cyclic time plans supported |
| ISP address library | Default ISP address libraries: China Telecom (CHN), China Mobile (CHN), China Unicom (CHN), CERNET (CHN), and Beijing Teletron (CHN); customizing, importing, and exporting ISP address libraries |
| Virus protection template | Configuring content object templates; antivirus (AV) templates supported |
| Configuring virus protection templates; configuring quick scan or deep scan; configuring templates based on protocols and directions;setting excluded viruses |
| Intrusion prevention template | Configuring content object templates; intrusion prevention (IPS) templates supported |
| Configuring intrusion prevention (IPS) templates; configuring rule filters based on objects, severity, protocols, threat types; setting excluded rules |
| SSL proxy certificate | Adding, importing, deleting, viewing, and downloading SSL proxy certificates; configuring a global SSL proxy certificate |
| Server certificate | Importing, deleting, viewing, and downloading server certificates |
| Security rule base | Viewing default security rules in the IPS library |
Policy |
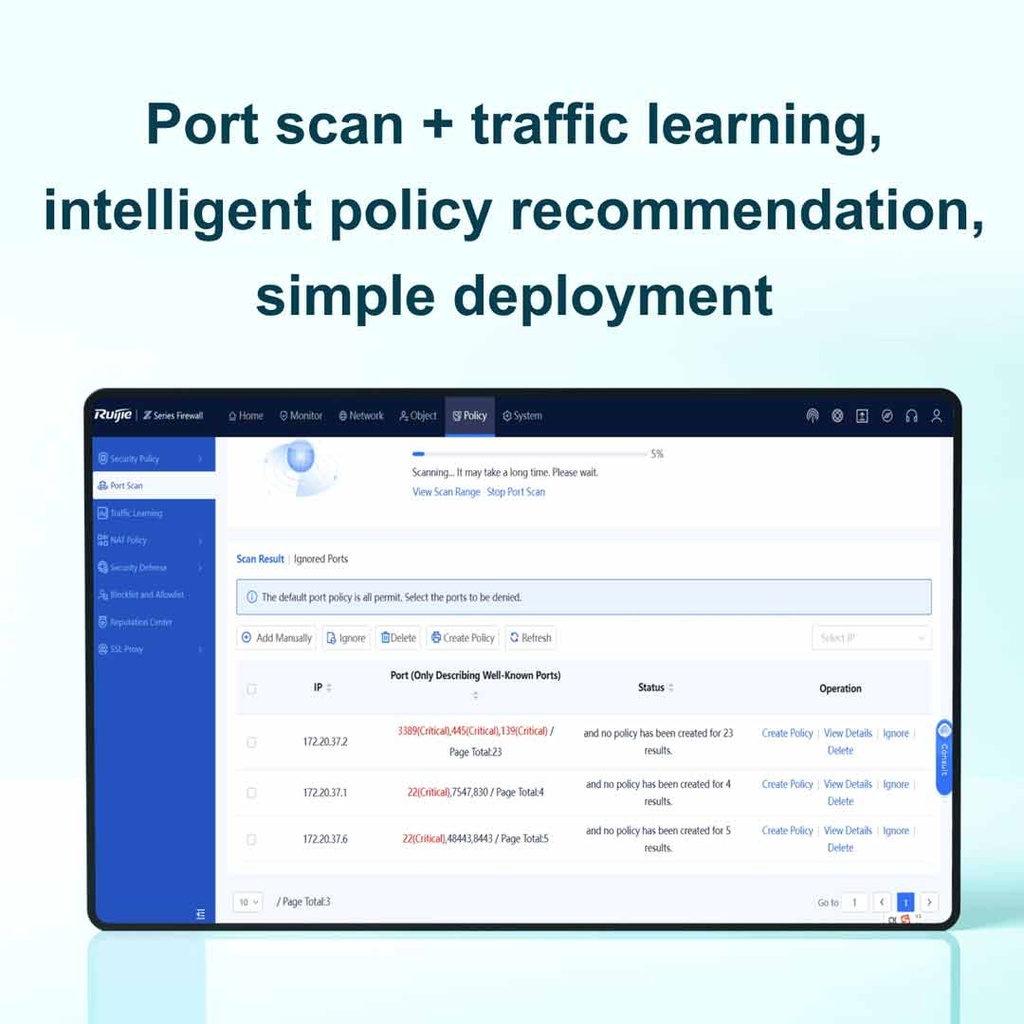
| Traffic learning | Traffic learning to record destination IP addresses and port numbers as well as abnormal traffic |
| Export of traffic learning logs |
| NAT | NAT and NAT policies |
| Policy import | Batch import of NAT policies |
| ALG | Common NAT ALG services in NAT policy |
| Server mapping | Server port mapping in NAT policy |
| Address pool | NAT address pool status display in NAT policy |
| Security policy | Configuring security policies; customizing policies based on parameters including objects, contents, and zones; policy list |
| Batch import of security policies |
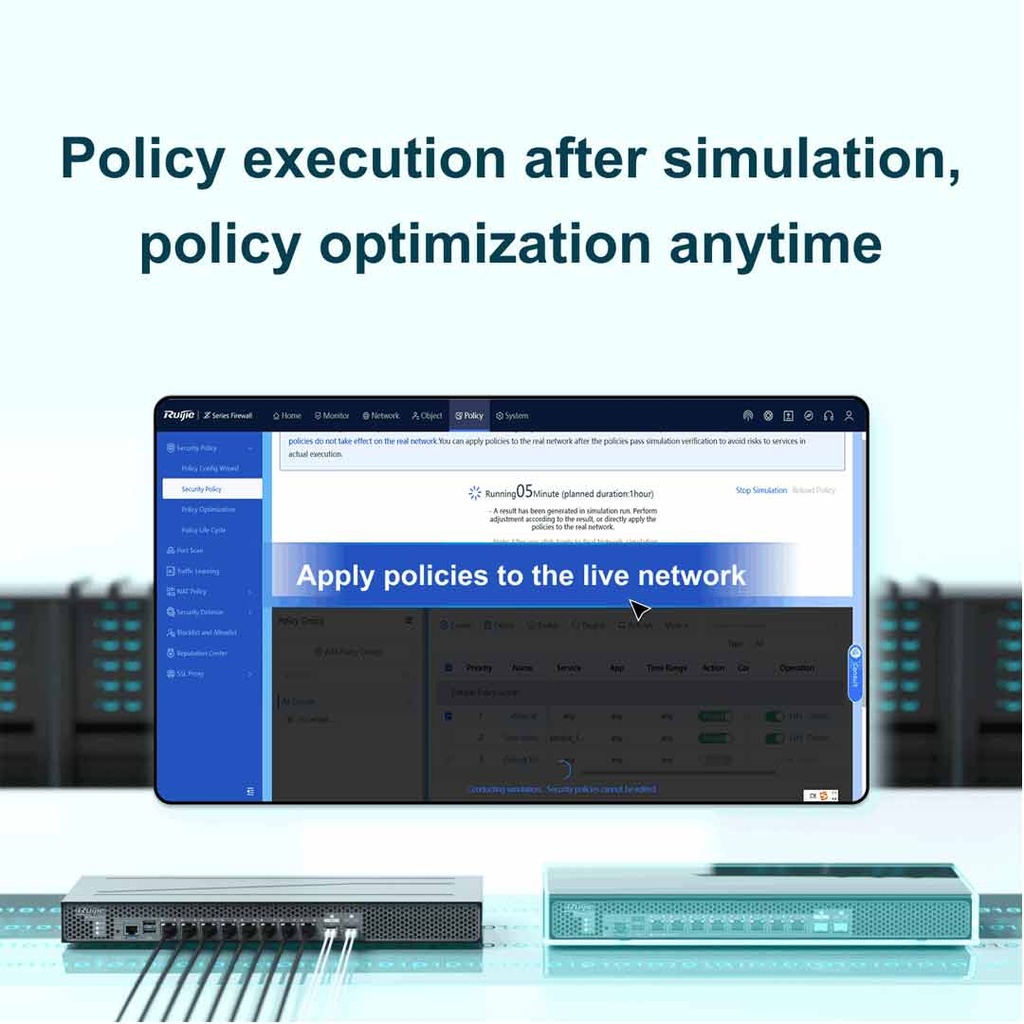
| Simulation policy | Simulating policy execution in the simulation space to check whether uncertain security policies can achieve expected effects |
| Policy configuration wizard | Security policy configuration wizard for conducting port scan, performing configurations, testing configurations, and other steps to generate security policies |
| Policy optimization | Sorting out configured security policies and analyzing policies to identify redundant, expired, and conflicting policies |
| Policy lifecycle | Full lifecycle display of security policies, including detailed records of policy changes |
| Port scan | Port scan of configured IP ranges for all ports or selected ports; policy creation prompt for scan results |
| DoS/DDoS attack defense | Different DDoS attack defense policies in security defense |
| ARP attack defense | Anti-ARP spoofing, ARP flooding suppression, and other functions in security defense |
| Local defense | Configuring local defense policies in security defense |
| Threat intelligence | Enabling or disabling threat intelligence; customizing threat intelligence; managing excluded threats |
| Blocklist and allowlist | Configuring global blocklists and allowlists |
| SSL proxy policy | Configuring SSL proxy policies; customizing policies based on parameters including objects, contents, and zones; policy list |
| SSL proxy template | Configuring SSL proxy templates; setting the template type to protecting client or server |
| Allowlist | Configuring domain name allowlists and application allowlists |
System |
| Administrator | Creating device administrators, including account names, passwords, and description |
| Administrator role | Setting multiple administrator roles and assigning different permissions |
| Clock configuration | Configuring system time; NTP service configuration supported |
| SNMP | Connecting to third-party platforms for management through SNMPv1/v2/v3 |
| Service parameter | Configuring service ports for a device, including web (HTTPS), SSH, and other ports |
| Authorization management | Managing licenses of devices, including license import and activation |
| Device information | Viewing device information, including the product name, SN, and MAC address, version information, running time, and license information |
| System restart | Restarting the system on the web UI |
| System upgrade | Upgrading the system |
| Patch installation | Downloading and installing patches for upgrade |
| Configuration backup | Import and export of devices configurations |
| Factory settings restoration | Restoring factory settings on the web UI |
| Signature library upgrade | Automatic signature library upgrades based on the latest versions on the cloud |
| Cloud management platform | Enabling or disabling unified management on the cloud management platform |
| Device binding | Adding devices to the cloud management platform by scanning a QR code |
| Ping | Ping for troubleshooting |
| Tracert | Tracert for troubleshooting |
| Packet obtaining tool | Tool for obtaining packets and exporting results |
| One-click collection | Collecting fault information with one click |
| Device health | Device health diagnosis |
| Service diagnosis | Service continuity diagnosis |
| Breakdown record | Breakdown information records |
| Device log retention | Device log retention |
| External APIs | RESTful APIs for third-party interconnection |